Hello everyone. I'm a user from Korea, and I joined this community yesterday to ask a question about a circuit I'm building. While I have a better understanding now, I had to delete my original post due to an image issue. I've now prepared a new post to clearly explain my question again.
First, I apologize for the previous post. I removed the image because I did not have permission to use it and only left a short "thanks" message. I've now created a new diagram and am re-uploading it.
My previous question was about the unique bypass wiring I found on a Decimator G-String PCB and how it works.
I was previously familiar with the bypass method uploaded by Cybercow on this forum: https://forum.pedalpcb.com/threads/decimator-ii-g-string-vca-noise-gate.20155/.
However, on another website, I found a bypass wiring diagram like the one shown below.

My previous question was difficult for me to understand initially, even though I now roughly know that this method bypasses the 2181 IC. I could intuitively understand how bypass works from the method provided by Cybercow, but this other method was hard to grasp.
I can't analyze this perfectly because I'm not an expert, so my explanation might not be precise. I've mostly solved the problem, but I drew a new diagram to share what I've learned with all of you.
First, I apologize for the previous post. I removed the image because I did not have permission to use it and only left a short "thanks" message. I've now created a new diagram and am re-uploading it.
My previous question was about the unique bypass wiring I found on a Decimator G-String PCB and how it works.
I was previously familiar with the bypass method uploaded by Cybercow on this forum: https://forum.pedalpcb.com/threads/decimator-ii-g-string-vca-noise-gate.20155/.
However, on another website, I found a bypass wiring diagram like the one shown below.
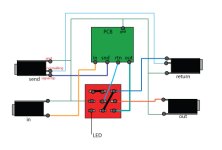
My previous question was difficult for me to understand initially, even though I now roughly know that this method bypasses the 2181 IC. I could intuitively understand how bypass works from the method provided by Cybercow, but this other method was hard to grasp.
I can't analyze this perfectly because I'm not an expert, so my explanation might not be precise. I've mostly solved the problem, but I drew a new diagram to share what I've learned with all of you.
Last edited:
